Qubes OS Tutorial: Security By Isolation
Thursday August 23, 2018
Qubes OS is a distribution of Linux with security as its focus, and it does it very well. At its core it’s based on Fedora and utilizes the Xen hypervisor to achieve security by isolation. Qubes can take a bit to get used to and it has its quirks but generally works quite well and has been stable for years. To run the latest stable version of Qubes you’ll need to have a nice x86_64 CPU that supports Intel VT-x & VT-d or AMD-V & AMD-Vi. You’ll also want a hefty amount of RAM (I have 20GB) depending on how many VMs you’ll be running and an SSD. I’ve been using Qubes as my daily driver for years and I can say it’s the real deal when it comes to desktop security.
Usability of Qubes OS
One of the most important factors in a desktop OS is its usability and looks. It has to function and look well! By default Qubes 4.0 will run the Xfce desktop environment, which has been one of my favorites over the years.
It’s very lightweight and customizable. You’ll be able to move around and fit the Xfce panel, change coloring and theme to your liking, as well as adding a few widgets while you’re at it. My desktop might be plain but it’s how I’ve had it for years and it works the best for me.
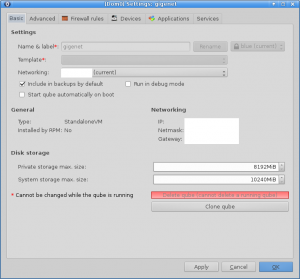
One of the best parts about Qubes is the Qubes Manager, it gives you an overview of all the VMs you’ve created along with the ability to customize everything about them. While I like to use the CLI to perform most actions it’s nice to customize settings in a GUI. Here is a screenshot example of the basic options.
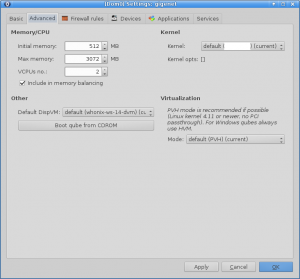
Along with the advanced settings.
Structure of Qubes
The structure of Qubes is similar to your typical hypervisor. Specifically, if you are familiar with Xen you will have an easy understanding of how it works. In Xen there are something called domains which are simply virtual machines or ‘VMs’. Dom0 is the privileged/root domain that controls DomU which are unprivileged domains.
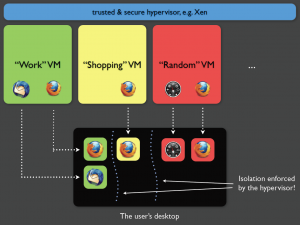
In this article I am just going to be calling DomU, VMs for simplicity. Dom0 is able to access hardware directly and assign the controllers to VMs as needed.
For example, in a default Qubes 4.0 setup the installer will allow you to setup 2 important VMs, sys-usb and sys-net. sys-usb will hold the USB controllers of your device so that any USB device attached is only exposed to sys-usb and not directly to Dom0. The same goes for sys-net which will hold your wifi and ethernet controllers. This is important because exploitation through these controllers if they were attached to Dom0 would be fatal.
If Dom0 is compromised it’s game over. The overall concept is that anything you do besides administering the VMs and installing Dom0 updates should be done through a VM. Hence security by isolation.
Qubes VM Types
In Qubes there are a few VM types. AdminVM (Dom0), TemplateVMs, Template based AppVMs, standalone AppVMs, standalone VMs not based on a template and DispVMs.
- TemplateVMs: A TemplateVM is a VM that is to be used by AppVMs as a template for themselves. For example, you can install a Fedora 28 TemplateVM and configure the software you’d like for use in your AppVMs.
- AppVMs: By default all of the running VMs in Qubes (besides Dom0) will be template based AppVMs. These VMs are almost entirely volatile besides the user’s /home directory which is bound to /rw. This is an important design concept because if a VM is compromised you can simply shut it down and start it back up with a clean slate. You can set files to persist with some configuration however. Standalone AppVMs are a bit different, instead of being volatile everything persists on a shutdown. At creation time it copies the TemplateVM and makes its own image. I generally prefer these as they’re easier to work with and you don’t need to install all of the software you need in your TemplateVMs. Although, they are arguably not as secure as a template based AppVM.
- Standalone VMs: Standalone VMs not based on a template will require an installation source such as an ISO and are comparable in functionality to how you would manage a VM in VirtualBox. With these VMs you can practically run anything that will boot on top of Xen and x86_64, including Windows, just be prepared to add more RAM to your system!
- DispVMs: DispVMs or Disposable VMs are machines that you can spin up at will, they are based on templates and you can open anything from an existing VM on a DispVM. They’re often used to open unsafe or questionable documents that you wouldn’t trust in your normal VMs and the DispVMs themselves are entirely volatile. Nothing is written to disk and when you close everything inside of the VM, the VM is shut down and gone forever. I find them most useful when opening email attachments or files such as PDFs that I don’t trust.
Qubes Review Summary
Overall Qubes OS is my favorite distribution of Linux because it’s really all you need. You can run Linux, BSD or Windows all on one computer and you’re able to do it securely. Stop with the dual boot hacks, just use a hypervisor! Although it’s not going to run games smoothly, who uses Linux for that anyways? I find it especially useful if run on a laptop. I can bring all of my work environments everywhere I go. There’s no need to cram everything onto one cluttered desktop with Qubes.
If you’re interested in giving Qubes a try have a look at their documentation for further details. No one explains it better than the creators themselves.
Sound like a bit too much? Chat with our experts.